On the morning of October 28 this year, the University of Vermont Medical Center (UVMC) found itself dealing with a cyber attack that almost halted its operations. UVMC staff found themselves relying on pen-and-paper records and fax machines to stay operational.
It’s a chilling reminder that sound information security practices and controls are a non-negotiable for every business.
As the security of businesses’ information assets becomes increasingly important, ISO27001 sets the standard for protecting them from unscrupulous entities. The ISO27001 standard stipulates guidelines organizations should follow when managing their information assets’ security assets using an Information Security Management System (ISMS). As an internationally recognized standard, ISO27001 provides a framework for the leadership team and managers to security controls as it applies to the needs of the organization. It initiates an honest conversation on security within the organization and a recognition from all employees that information security is a responsibility they bear to the organization.
Most organizations operate digitally, and it has become second nature to most of us to store documents and other intellectual property in this format. ISO27001 is an international standard created to help organizations protect their data, by providing guidelines to establish and run an Information Security Management System (ISMS) that will best meet their needs.
Establishing an ISMS for your business is an opportunity to review your security protocols and practices with your leadership and your employees, and create a path forward that everyone can play a part in.
Top 5 myths about ISO27001
1. Myth: It’s the IT department’s responsibility
Information security is everyone’s the responsibility, and as you go through the standard, and its implementation, you’ll quickly come to that realisation. People mistakenly assume information security needs programming skills and other technical expertise, but it’s designed for everyone to use and understand.
For your senior management team, information security should be the driving force behind strategic procurement decisions, such as software and other assets, taking into consideration matters like what methods you’ll be using to preserve business and client data. Your middle managers are the overseers of your company’s IT-related policies, managing how processes are implemented, and what training their teams need. It’s up to everyone, no matter what level they are in your organization, to adhere to the set policies, use approved systems, and develop their security skills.
2. Myth: We only need to write policies
While ISO27001 puts a strong emphasis on documentation, it’s the adherence to that documentation that’s most important. The main purpose of ISO27001 standards in your ISMS is to act as a guide for you to implement best practice processes and procedures for operating securely. If you decide to become an accredited organisation, the auditor will expect to see proof that you’ve actively implemented your documentation.
1. Myth: Getting certified is just good for marketing
For some organizations, getting the certification mark is for appearances only – once they’ve got it, they have no intentions of implementing the recommendations from the standard, or fixing any deficiencies. While being accredited is a great marketing plus, it shouldn’t be your sole reason for getting it. There should be an internal need to boost your business’s security practices, and an alignment to your obligations and strategy before you embark on the accreditation journey.
2. Myth: We have fewer than five systems, so we don’t really need it
Any organization can implement ISO27001 as part of its ISMS, whatever its size, and however many (or few) systems it has in place. ISO27001 doesn’t just focus on systems and software; rather, it presents a best practice guide for implementing secure practices for all aspects of your business. The standard is discretionary, not prescriptive – not all the controls it sets out will apply to your business. You can customise it to suit.
3. Myth: Having the accreditation will scare attackers away
Having your business ISO27001 accredited won’t make you immune to attacks. Once implemented, the standard simply points out where there are vulnerabilities in your business so you can take corrective action.
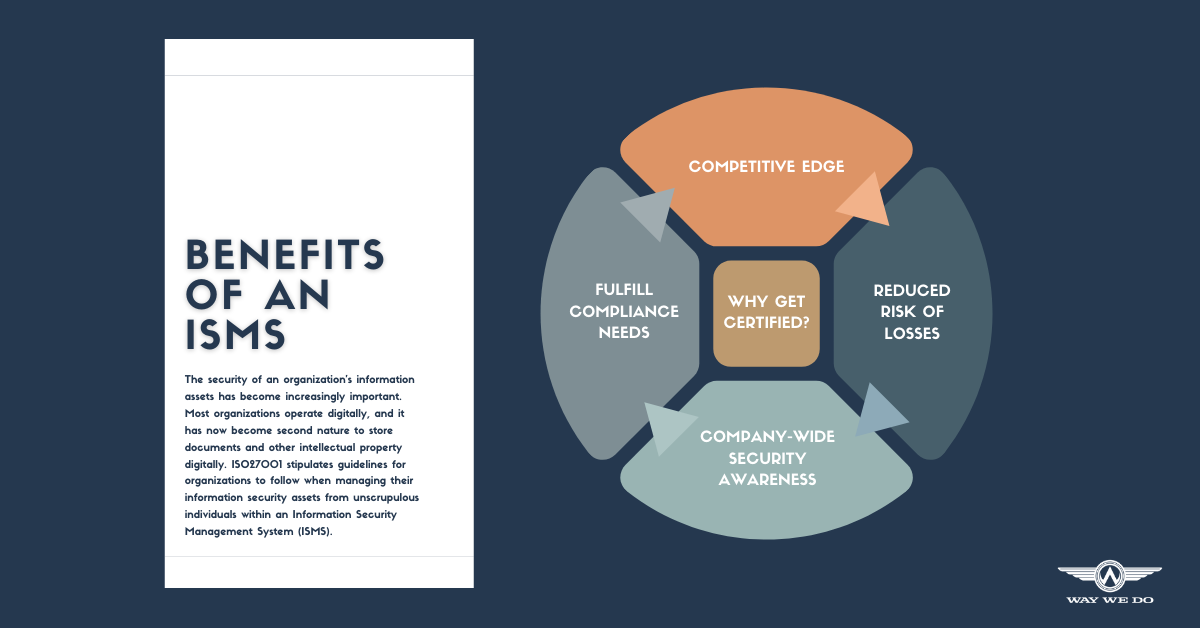
Why get ISO27001 certified?
It gives you a competitive edge
Getting your business ISO27001 certified gives you the opportunity to show your customers and potential investors that you’re committed to maintaining information security best practices. It can be a deciding factor in winning new work and staying ahead of your competition.
It reduces the risk of losses due to a security breach
From 2014 until 2018, hackers were able to access confidential client data from Starwood Hotels, which were bought out by Marriott in 2016. This breach exposed sensitive information – such as passport numbers, credit card details, and travel information – from 500 million customers. Of this 500 million, Marriott believes 100 million customers had their information stolen.
A security breach discloses confidential information, putting those affected at risk of being victims of other crimes such as identity theft. This can cause irreparable damage to your organization’s reputation as a trusted supplier, and put you in violation of regulatory requirements. The information your organization retains, whether it’s valuable or not, can prove costly to your business if you don’t take adequate measures to secure it. And remember, it’s not just client data you need to protect; it’s also your own financial information, and intellectual property you’ve developed over years in business.
Implementing the standard won’t make you invulnerable, but adhering to it will help you make sure you’ve got the right defences in place to make losses less likely. It also helps ensure continuous data integrity and privacy for all your client and business information.
It boosts your team’s security awareness
While you may have various technical solutions to protect your business from data breach, there’s always the human factor to consider. When it comes to protecting your information security, your team is an important point of defence. As a business owner and employer, you rely heavily on your staff (including contractors) to do the right thing and keep the company’s best interests at heart.
Make sure they’re aware of how to detect signs of a security breach, and that they’re attentive when they’re dealing with customer and business data. And make sure they have the right training and equipment to support them. ISO27001’s guidelines ensure each employee, regardless of their role within the organization, is adequately trained and that they understand their individual duties and responsibilities where information security is concerned.
It helps you meet legal, contractual and regulatory compliance
Implementing an information security standard like ISO27001 ensures any controls you implement comply with current regulatory requirements – national, international, and industry-wide. And when you’re compliant with regulatory requirements, there’s less need for frequent audits.
Getting certified
Before you get started with certification, you first need to have an understanding of whether certification will be important or if simply implementing the standard’s controls will be sufficient to meet your compliance needs. If you do decide certification is the path forward, you’ll need to go through the following six stages.
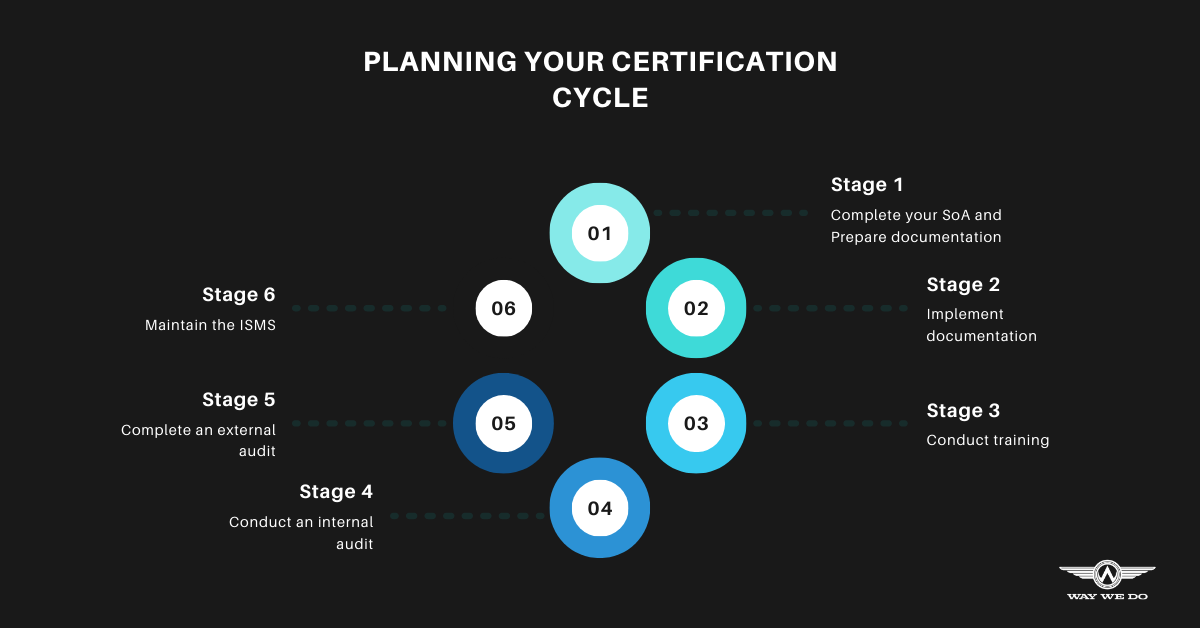
Stage 1: Complete your Statement of Applicability and prepare your documentation
A key requirement of your ISMS is sound documentation on how your organization implements and manages information security. There are two ways you can go about this activity.
If you’re new to certification, have no documentation, or feel your current ISMS documentation insufficient, you may want to start by completing the Statement of Applicability (SoA). An SoA helps you scope your ISMS. It will help you determine what requires documentation in your ISMS, what risks currently exist in your business, how to manage those risks using your ISMS, and how to assign responsibilities within your team.
If you’ve already got extensive documentation and have been through certification before, completing an SoA can help you identify gaps in your ISMS, which controls need updating, and any business areas that need additional risk management measures.
Once you’ve identified these elements, you can start creating, documenting, or updating your ISMS in Way We Do. The collaborative nature of Way We Do means multiple editors can work on content at any time. To help you capture the right information, editors can leave feedback for the author during reviews before they publish the final versions for everyone to access.
Stage 2: Implement documentation
Of course, you’ll need strong evidence of implementation during the audit stage of your certification journey to make sure the processes work as expected in your organization and your ISMS’s contents are relevant to your current operations. You’ll also need to conduct risk assessments to determine where you currently fall short and what controls you need to implement to address any risks you’ve identified. Set up any assessments you need to carry out as activated checklists in Way We Do to capture activity records as evidence for your certification audit. Make sure your staff have signed off on policies, where appropriate, and that they’ve been involved in the implementation process.
Stage 3: Conduct training
Your team’s awareness of information security is a prerequisite and it’s important they understand their responsibilities to the organization and clients. It’s also important for employees to be aware of how to manage information security in their roles. Company-wide information security training is essential, as in an ongoing training initiative to ensure your team’s skills are up to date and your business meets compliance standards.
Stage 4: Conduct an internal audit
The internal audit captures your organization in its present state, and identifies areas where you need to take immediate action. Correct all identified issues before you move on to Stage 5, and produce evidence of these changes being implemented.
You can choose to have an internal audit team conduct Stage 4 for you, or hire an external agency with specialist expertise.
Stage 5: Complete an external audit
An external audit involves an independent auditor reviewing your documentation and your implementation from Stages 1 and 2, based on the ISO27001 standard.
Once completed, your auditor will send you your accreditation. You’ll then have further follow-up surveillance audits one and two years after accreditation, with a third-year re-certification audit to ensure you’ve maintained your ISMS as prescribed by the standard.
Stage 6: Maintain the ISMS
Certification isn’t the end. It’s important to maintain, and improve, your ISMS after certification. With your ISMS forming a part of your regular business operations, you’ll have less to worry about when audit time comes around. Here are a few things to keep a close watch on.
- Make sure you complete regular risk assessments, and implement any corrective actions straight away.
- Complete regular internal audits to make sure your business stays compliant.
- Conduct regular training and awareness programs for your team, and keep them up to date on any information security risks or threats.
Remember, everyone has a part to play in keeping your valuable business information secure.