The American Institute of CPAs designed the Service Organization Control (SOC) report to create a clear framework for vetting service providers that process and safeguard business data. SOC reports provide a level of assurance to organizations that have outsourced critical business operations and are concerned about information security.
SOC reports help service providers clearly articulate their internal controls and environment as they relate to processes that can impact business data. For users, SOC reports give them the assurance they need that their service providers have the right tools in place to protect their interests and their privacy, and effectively manage their data.
To get an SOC report for your business, you’ll need to engage an independent CPA or accounting organization to conduct an audit. Once they’ve completed the audit, you’ll get a report you can then give to your current and prospective clients that sets out your internal controls, and their effectiveness.
Types of SOC Reports
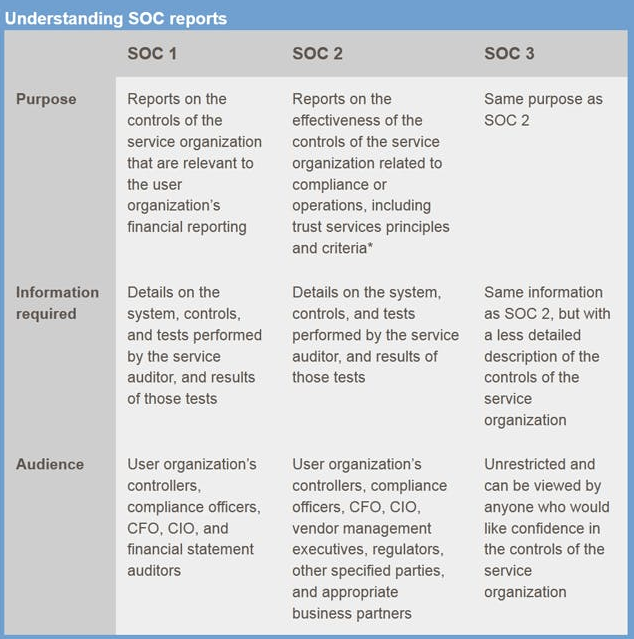
SOC reports come in three main forms: SOC1, SOC2, and SOC3, each with their own distinct purpose. Which type of report you’ll need is something you’ll need to discuss with your audit professional, and will depend on your specific needs, and the related objectives you’re trying to achieve.
SOC1 Reports
This type of report sets out a business’s internal controls as they relate to financial reporting. Specifically, their accounting and financial controls, and vets how they manage their books. SOC1 reports can be further classified as Type I and Type II: Type I refers to an audit conducted at a particular point in time; whereas Type II refers to audits conducted over a set duration.
SOC2 Reports
This type examines the internal controls of the service organization based on one or more of the five Trust Services Criteria, namely:
- Privacy
- Security
- Availability
- Confidentiality
- Processing integrity.
The Trust Services Criteria define the principles by which a service provider manages customer data. SOC2 reports can also be classified into two types: Type I refers to the vendor’s system and its suitability with respect to the Trust Services Criteria; and Type II reports on the system’s operational effectiveness and efficiency.
When conducting an SOC2 audit, the external auditor must review multiple elements under each of the five criteria.
- Privacy: Reviews the system’s ability to collect, use, retain, disclose, and dispose of personal data according to the organization’s policies. This can be personal information, such as social security numbers, address, health status, ethnicity, sexuality, and so on.
- Security: Reviews the system’s security against access control measures that exist within it. This criterion also evaluates controls against unauthorized access, unauthorized removal of data, misuse of the platform, and unauthorized data alteration.
- Availability: Assesses the system’s availability for operation and use by your organization, as set out in providers’ Service Level Agreements, to meet your objectives. Functionality and usability are not a concern for this criterion. Rather, incident handling, failover restorative practices, and performance.
- Confidentiality: Evaluates how the system manages data that has been designated as confidential, and the safeguarding features available in the system. This criterion assesses things like firewalls, encryption, and access controls.
- Processing integrity: A system must always achieve the purpose it was implemented for. This criterion assesses whether the system receives information and delivers it to the right user at the right time. The main focus of this criterion is that the system fits the purpose it was procured to fulfil.
SOC3 Reports
SOC3 reports are similar to SOC2s, in that while it presents the same findings, an SOC3 report provides a general summary instead. An SOC3 report simply presents information on whether the service provider has achieved any of the Trust Services Criteria, and confirms the findings of an SOC2 report.
SOC for Cybersecurity
Organizations who provide SaaS products and services can use this reporting framework to demonstrate how adequate their cybersecurity controls are. The AICPA’s article SOC for Cybersecurity is an excellent source of information and resources if you’d like to find out more.
Who needs the information in an SOC Report?
The final format of each type of SOC report depends on who your final audience will be.
The findings from a service provider’s SOC1 report go to their client’s Financial Controllers — for example, the Chief Financial Officer and Chief Information Officer.
SOC2 reports are more sensitive than SOC1 reports, and can be reviewed by the same audience in the client organization, including other members of the C-Suite. However, a service provider can also make the report available to its regulators and approved business partners. We recommend SOC2 reports only be shared after exchanging a Non-Disclosure Agreement with the receiving party.
SOC3 reports have no restrictions, and anyone can view them. Most service providers can display their SOC3 report on their website if they wish.
Getting the right SOC Report
If you’re looking to outsource any business operations, you may need to ask for an SOC report from a Vendor. Before you do this, you’ll need to determine which is the right report for you. The choice of report will vary depending on your service needs, so it’s important to understand the purpose of each.

If you’re a service provider, you’ll need to engage an external auditor to complete your certification. Your auditor will assess your organization and system based on the type of SOC report you want. Choosing the right SOC report for your organization is critical, so before you embark on your SOC audit journey, ask yourself these questions.
- What type of services do we offer our clients?
- Who is our audience, and what information are we trying to relay to them?
- Do we need an SOC report? And if yes, which reports do we need?
- What image do we want to present to our clients, both current and prospective?
- How often will we provide SOC reports? (Note, once a year is considered the norm, but your clients may expect them more frequently.)
With the answers to these questions clear in your mind, you can make a choice as to whether or not getting an SOC report is right for you. Of course, if you do decide to go ahead, you’ll need to get prepared.
Preparing for an SOC Audit
The primary purpose of an SOC audit is to demonstrate the service organization has the appropriate controls in place to address information security and compliance concerns. Before you invite an external auditor into your business, make sure you’ve made the following preparations.
1. Review your client base
This will help you understand who your clients are, their specialities, and the internal controls that are essential to them. This information will help you align your internal controls to their needs.
2. Review, update and assemble your operations manual
Make sure you’ve got all the necessary policies and procedures prepared and compiled in your operations manual. These policies and procedures will serve as evidence that you have the right controls in place.
But it doesn’t end there. Carry out regular reviews and updates to keep your operations manual current and in line with existing business practices. For instance, a comprehensive Backup Policy and corresponding Backup Procedure can demonstrate your implementation of Availability Criteria.
Of course, a well-documented manual can become meaningless if there’s no evidence that your employees are complying with it. You also need to implement a process that tracks employee training, or a means of monitoring that they’ve read and understood your policies with respect to service provision and how this relates to Security Criteria.
3. Perform a self-assessment
A self-assessment can help you identify any gaps in your control environment before an external auditor comes in. And once identified, you can correct any gaps ahead of an audit to give yourself the best chance of success.
4. Define the scope of the audit
Defining a scope for you audit will help you identify what goals you want to achieve, and what learning outcomes you expect to get for your organization.
5. Confirm and address any regulatory compliance obligations
The nature of your business determines what other compliance requirements you need to meet, and your auditor will review what controls you have in place to address them. These other regulatory obligations may also feed off your client locations and what obligations their vendors must fulfil. Having a thorough understanding of your clients is essential.
6. Review your SLAs
Your SLAs outline your service delivery controls to your clients. They also outline your service practices and set out how much risk you’re willing to take on. This helps both you and your clients get a closer look at how acceptable the risks are for you both.
7. Conduct a readiness assessment
An SOC audit can take anywhere from four to 24 weeks, so it’s important to make sure you’re ready on time. Conducting a readiness assessment will evaluate how audit-ready you are. This assessment identifies areas in your controls that fall short of the acceptable standard. You should engage an independent external auditor for this assessment. Also, ensure that the auditor is CPA certified.
Get yourself ready using Way We Do
Your Way We Do integrated management system is more than just a repository. It’s in a prime position to help you get ready for your audit.
1. Your Way We Do integrated management system is about more than just storing your policies and procedures. It also gives you several reporting tools you can use to provide evidence during your audit. For example:
-
- The Review History report shows how often you’ve reviewed a procedure, the reviewers involved, and the activities carried out during the review.
- The Edit History Report shows what changes you’ve made over the life of a procedure, the version number of the procedure, and the reasons behind each change.
- The Activated Checklist Instance Report demonstrates active use of your procedures, and collates the activities in each from start to finish.
2. Use Way We Do to carry out your self-assessment. Use the same Activated Checklist as your compliance officers to identify gaps in your internal controls. This should give you a review of risks related to your:
-
- customers
- financial controls
- management
- personnel
- technical controls
- resources.
3. As part of your self-assessment, you can also use Way We Do to test your internal controls. This can be particularly useful for carrying out tests related to one or more of the Trust Services Criteria for SOC2. For instance, the presence of editorial permissions in Way We Do demonstrates the availability of Access Controls under the Security criterion.
What being SOC-compliant can do for you as a service provider
An SOC report provides invaluable information to clients on prospective service providers. These reports ensure the services you provide are at a level that will help you meet any regulatory standards. Having an SOC report can offer you, and your clients, a range of benefits.
- Successfully passing an SOC audit gives your clients the assurance that your systems are secure. They get peace of mind, and you can quickly establish trust.
- An SOC report can boost your brand’s reputation as a business that complies with government and industry standards, giving you a competitive edge over those without similar ratification.
- Meeting your SOC compliance requirements gives you added peace of mind that you have adequate controls in place to catch any potential issues before they cause a security incident.
- Being SOC compliant boosts your systems’ cybersecurity resilience. Well implemented cybersecurity practices help you recover more quickly after an incident, and ensure your losses — if there are any — are significantly reduced.
How much an independent audit costs will depend on your business’s size, the reporting period, and what controls you select. You can expect the cost of subsequent audits to reduce significantly after your first one.
You may have also considered getting other forms of certification, for example ISO 27001, which is another framework for Information Security. Though similar in some control areas, there are still significant differences between each auditing framework. While ISO 27001 reviews the controls you have in place for your data and service providers, SOC reports — SOC2 in particular — examines your data environment as a service provider. However, both frameworks can work cohesively to help you implement the necessary controls and documentation to back it up.
Although it may seem a complicated process to go through, getting your SOC reports can help you build a more robust and competitive business. Feel free to reach out to the Way We Do team if you have any questions about what else the platform can do to help you decide on, and get ready for, an SOC audit.