Way We Do for CMMC and NIST 800-171 Compliance
Way We Do Cybersecurity
Maturity Model Certification
(CMMC) Compliance
Turn CMMC procedures into ACTIVE workflow
See how we make it easier
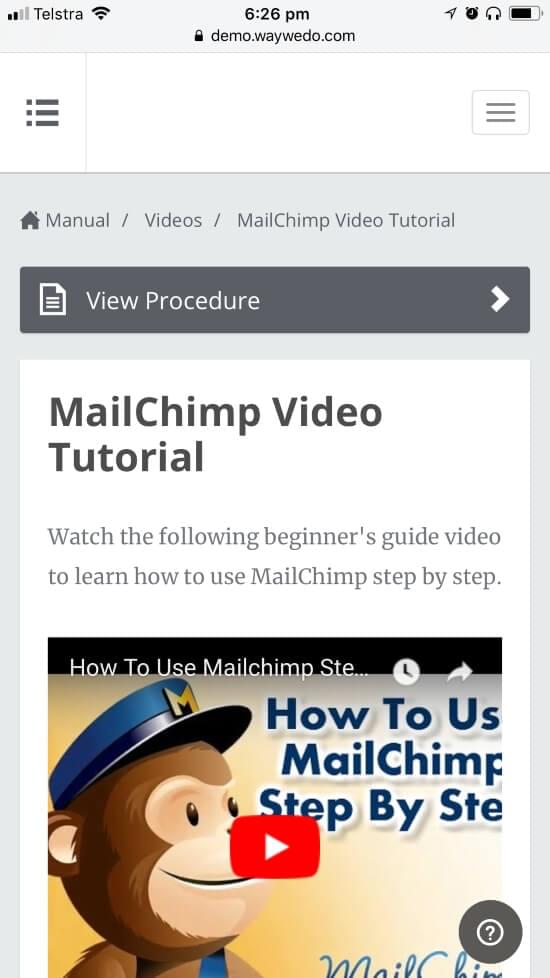
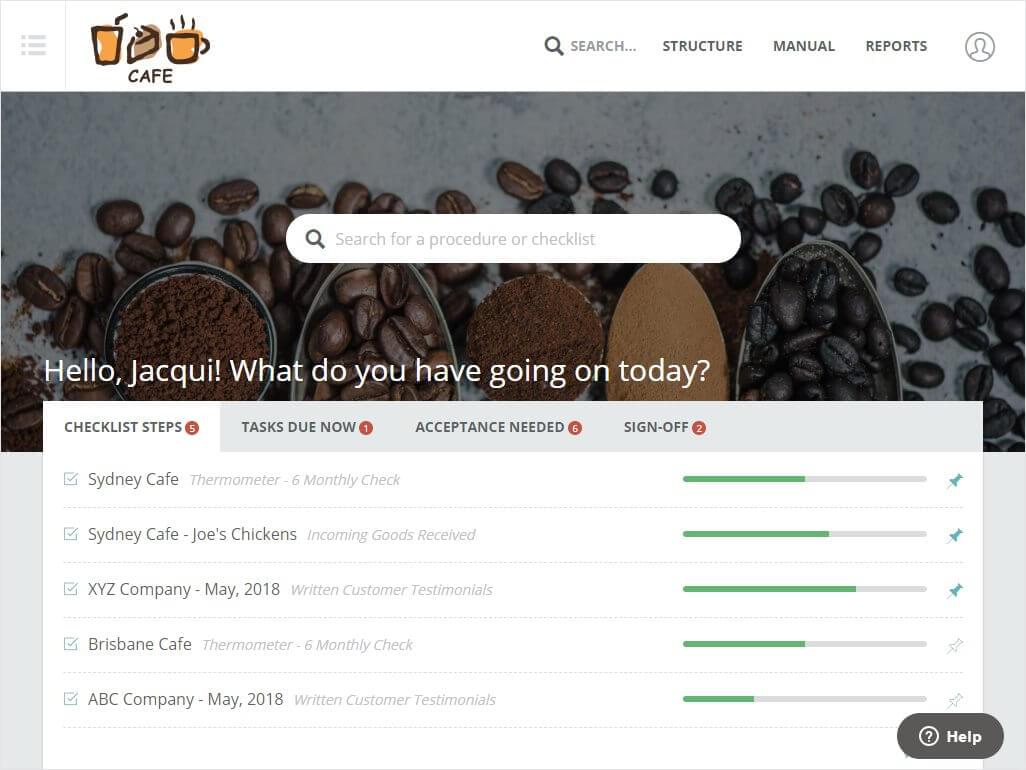
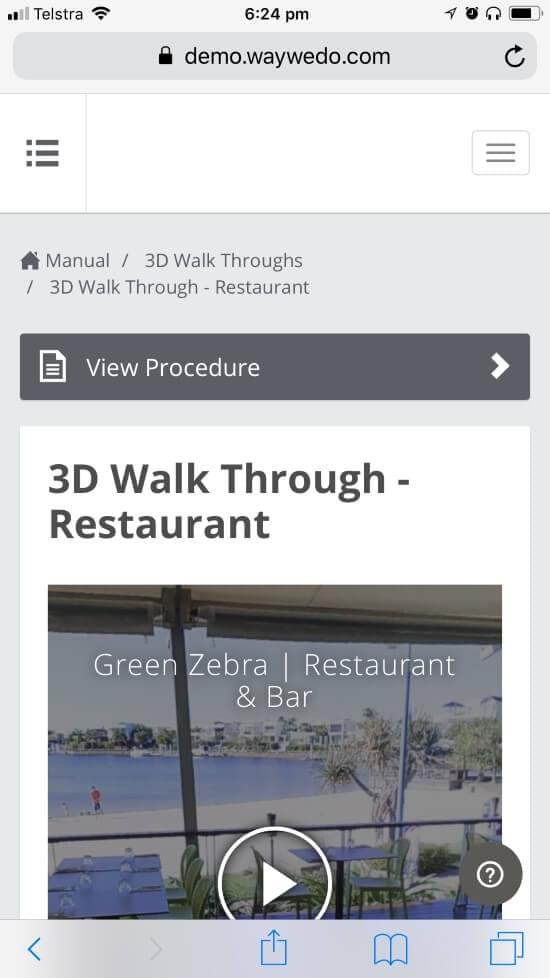
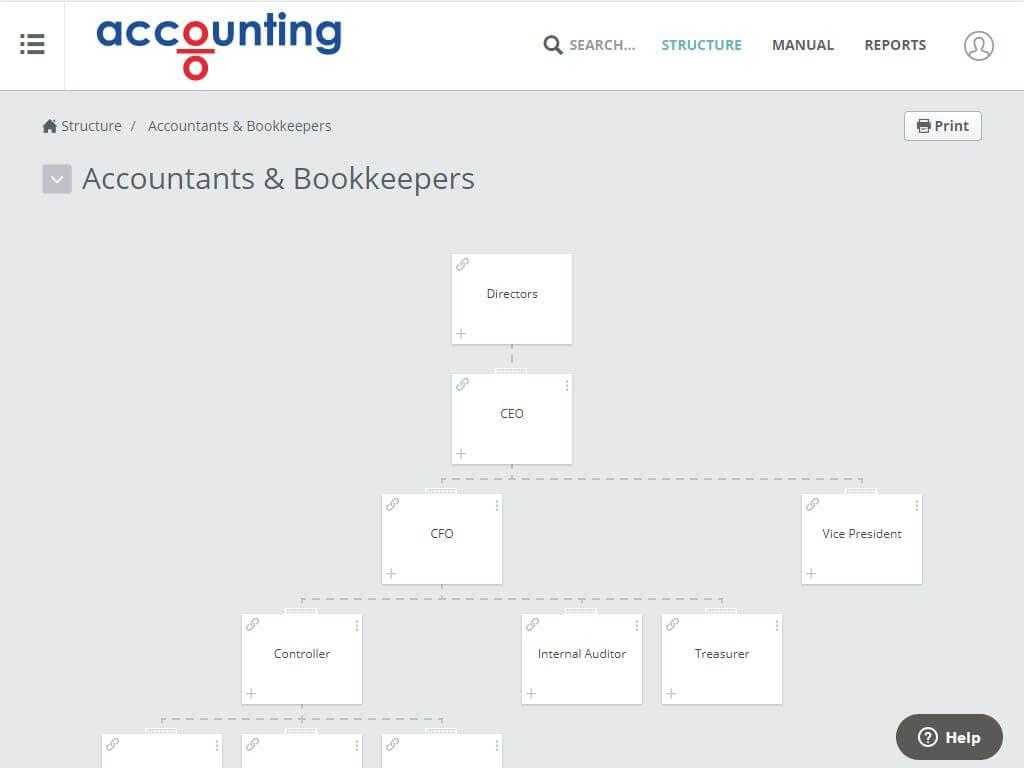
Use Way We Do for all your
requirements
Ready to get started?
Start your free trial today
No credit card required
Increase the ADOPTION of your CMMC PRACTICES
Way We Do for Information Security Management, enables organizations to implement an information security management framework including policies, processes, and procedures for the entire team to use. Way We Do turns static policy, process and procedure documents into active workflows, to close the gap between what is documented and what happens in practice.
Organizations are able to implement a user friendly, information security management solution that meets the requirements of ISO 27001, NIST 800-171, CMMC, FedRAMP, GDPR and other cybersecurity and privacy related standards. In turn, Way We Do raises the maturity level of an organization to adopt cybersecurity practices.
Centralize cybersecurity processes, policies and procedures.
Rather than being scattered throughout the organization, Way We Do enables all documented information security processes, policies and procedures to be centralized for all employees to access in the form of training modules, tasks and workflows, reference guides and audit checklists. All employees will understand their roles in regards to cyber security awareness and tasks.
Turn static documents into active and automated workflows
Cyber security governance requires security processes to be documented, however governing bodies, customers and auditors want to see evidence of these practices being adopted. Traditionally, documented policies, processes and procedures are static documents, that are often created and then forgotten about. The power of Way We Do turns static documents into active workflows to increase adoption and records completed activities.
Create training, workflows, reference guides and audits
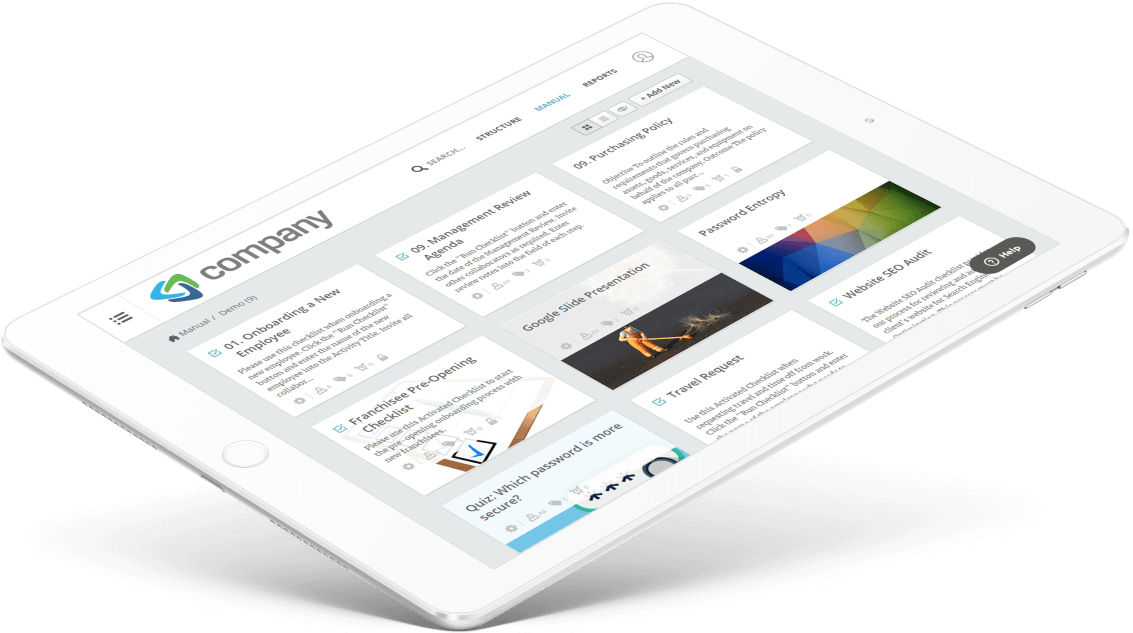
Way We Do’s “no code” Activated Checklists delivers multiple purposes and can be used in scenarios such as providing training modules, task workflows, guides and audit checklists. All of these scenarios are required for information security management.
- Setup: Create an Org Chart with cybersecurity roles, Setup Policies, Processes & Procedures
- Activate: Add Criteria to Procedures including Roles, Tasks, Acceptance, Revision Reminders and Integrate with 3rd Party Software to Automate processes
- Use: Use, Track & Measure Real-time Performance and Compliance
Thousands of users love Way We Do
See how our customers are transforming their businesses and organizations
A fusion of process, knowledge and compliance
-
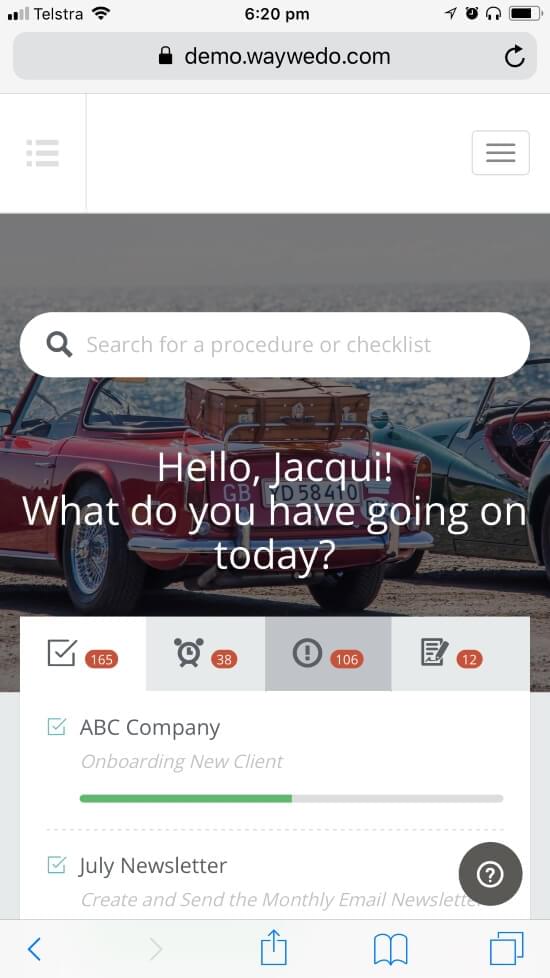
Increase adoption of your info security procedures with Activated Checklists
Way We Do helps people to remember to perform and complete important information security tasks across the company. Repeatable processes are scheduled for specific roles to perform, with multiple people participating in the same process.
-
Automate cyber security processes in Way We Do from triggers in 3rd Party Software
With over 2,000+ integrations with 3rd party software, processes in Way We Do can be triggered to run automatically. For example, when a new employee is added to the HR system, the onboarding and secure setup into IT systems processes are started and sent to the right people on the team to implement.
-
Report upon completed cyber security tasks
A key aspect of information security management is the reporting of required processes, their cadence and completion status. When security tasks and activities are completed, the name of the person completing the item is recorded, along with a time and date stamp. You will pass your audit in no time!





