Even the most creative organizations have policies, procedures and processes in place to help them stay on a path to success—even the Emmys. The high-profile event would not run as smoothly as it does without strict adherence to their PPP. If you’ve ever been in an amateur stage production, you’ll know the Production Manager has full control—and the Emmys takes this precision 1000 levels higher.
Remember. Always follow the script!
So what can go wrong? Well, having presenters “going off script” is a huge headache. Ad libbing in a LIVE production is a stage manager’s ultimate nightmare. Especially when actors have a political agenda to push. It can embarrass the Emmys brand, offend audiences, reduce money-making advertising time and alienate prime time advertisers. It can even lead to lawsuits. And that’s just for starters.
A good script keeps everything ticking along nicely; it’s a vital part of the Emmys process. Sure, they want presenters to infuse their personality and style into their delivery, but ultimately, to make things work properly, they must keep to the script!
Emmys – The Organization
The Emmys is more than an annual event on TV where the Hollywood elite get to rub shoulders. It’s a massive organization that runs multiple, area-specific ceremonies throughout the year to celebrate the achievements of the art and science of television.
Each ceremony has its “own set of award categories, nominating and voting procedures, and rules regarding voting committees”. Source: Wikipedia
Here are some of their policies.
- The Emmy statuette is presented to individuals, and not their employers.
- Emmy nominees and winners may refer to this fact in their advertising and publicity for up to 1 year after the award was bestowed.
- If the recipient is a regional nominee or winner, they must clearly state that the achievement is for a “Regional Emmy Award”.
- There is a correct and incorrect way of using the Emmy brand and trademark. Never use the plural for possessive form in the name. It’s “Emmys, not Emmy’s”. If you are lucky enough to win two awards, you can say “Two Emmy statuettes”, not “Two Emmys”.
- If the recipient or their heir wants to sell or dispose of the Emmy statuette, they are obliged to return it to NATAS (National Academy of Television Arts & Sciences). It will remain in storage in memory of the recipient
Source: National Academy of Television Arts & Sciences
Security and bodyguards are paramount to protecting actors, but who protects their data?
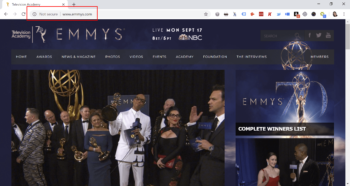
Obviously, there’s always room for improvement. And it seems they’re not managing their IT security as well as they could. There is no secure certificate on their website (we took a quick screenshot—see below). This begs the question of what other data security issues the organization may have. The Emmys event is one of the biggest on TV each year. The media attention it gets means it’s open not just to adoring fans, but trolls and hackers who might bring down the site, emulate it for their own ends, or create some other mischief that could harm the brand, or even the safety and security of others.
What might an IT “bodyguard” do? A draft process to protect Emmys data
Step 1: Know what data there is and where it lives. (Imagine if the personal contact details of actors were leaked to the Internet!)
Step 2: Authorize access to sets of data on a need-to-know basis only. Keeping tabs of who has access to sensitive data is critical.
Step 3: Bring in the Network Security big guns. Ensure firewalls and antivirus software are updated at scheduled intervals. Ensure employees’ own smartphone and tablet devices are covered by security policies and procedures. You do not want a junior runner sharing someone else’s private information on social media.
Step 4: Run data risk assessments regularly. Everything from power cuts and online data breaches to employee background checks needs to be considered, with a remedy plan in place that includes a PR strategy in case the brown stuff hits the fan.
Step 5: Keep daily backups of sensitive data, and regularly test the backup of the backup.